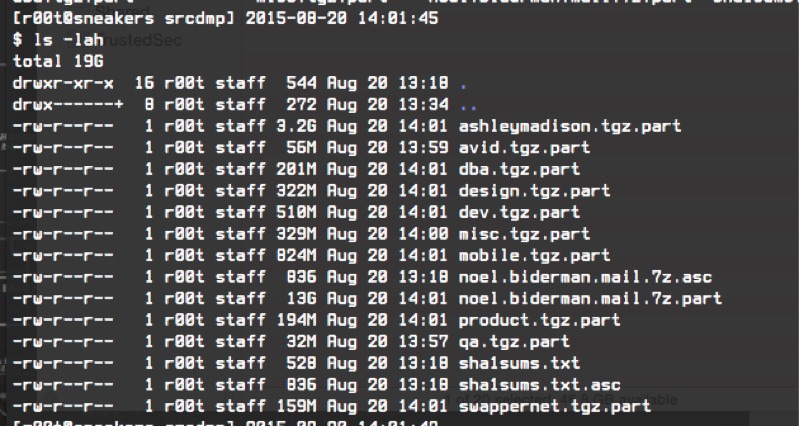
Data rate logger output of the Hack RF standard transfer test at 20 MHz... | Download Scientific Diagram
3D Hacking Code Data Flow Stream on Green. Screen with Typing Coding Symbols Editorial Stock Photo - Image of language, blockchain: 150730668
3D Hacking Code Data Flow Stream on Black. Screen with Typing Coding Symbols Editorial Stock Photo - Image of crime, hack: 150731378
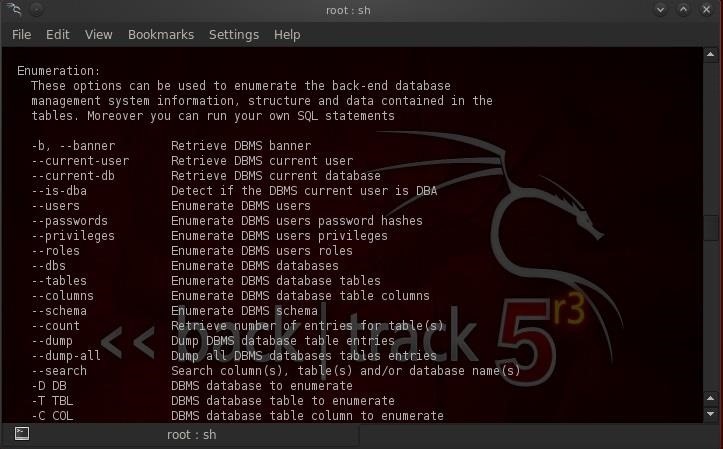
How to Hack Databases: Extracting Data from Online Databases Using Sqlmap « Null Byte :: WonderHowTo