
Li Xiong CS573 Data Privacy and Security Privacy Preserving Data Mining – Secure multiparty computation and random response techniques. - ppt download
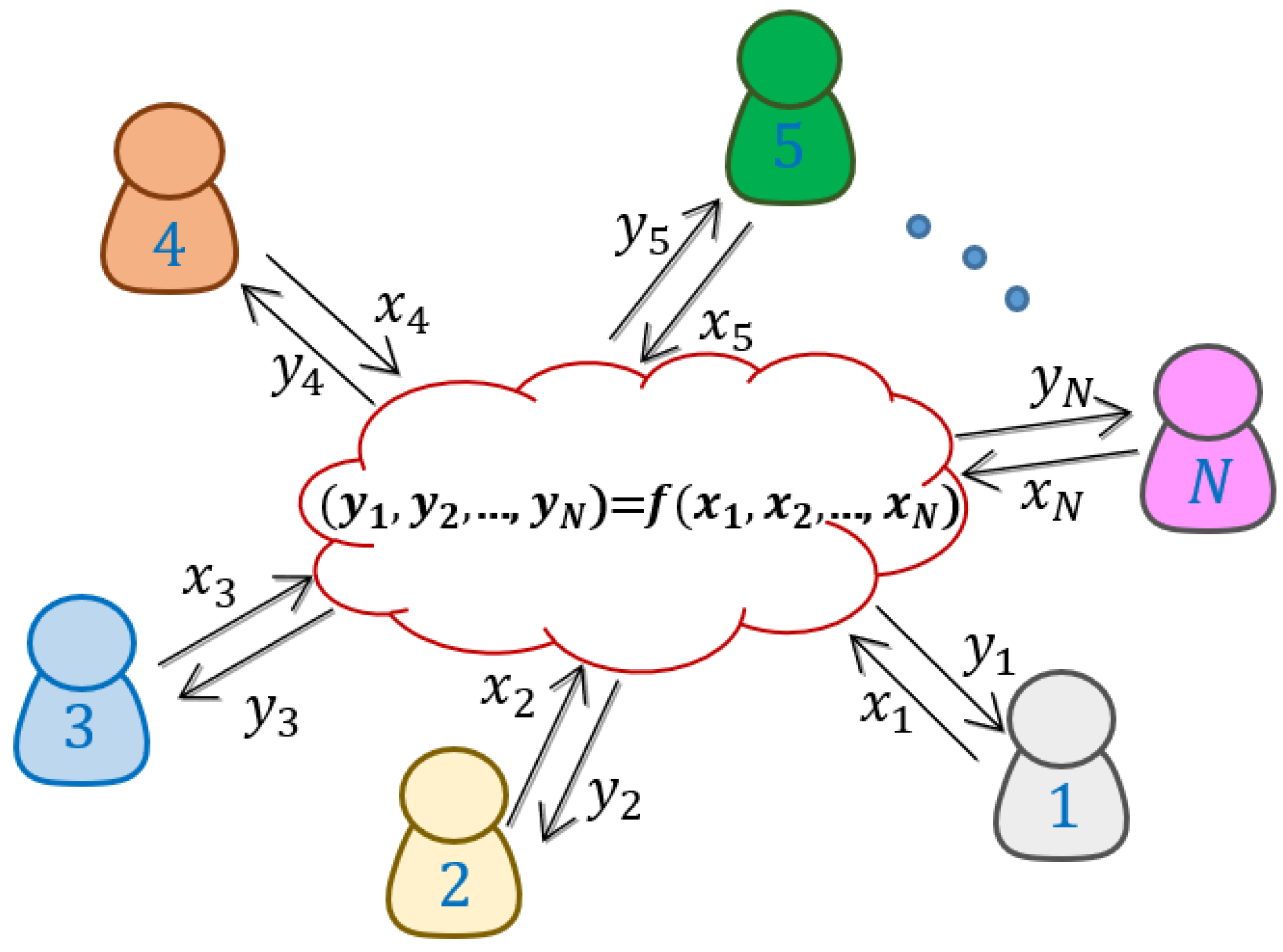
Applied Sciences | Free Full-Text | Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation

PDF) Fostering the Uptake of Secure Multiparty Computation in E-Commerce | Octavian Catrina and Octavian Catrina - Academia.edu

Privacy-Preserving Global Model Construction through Secure Multiparty... | Download Scientific Diagram
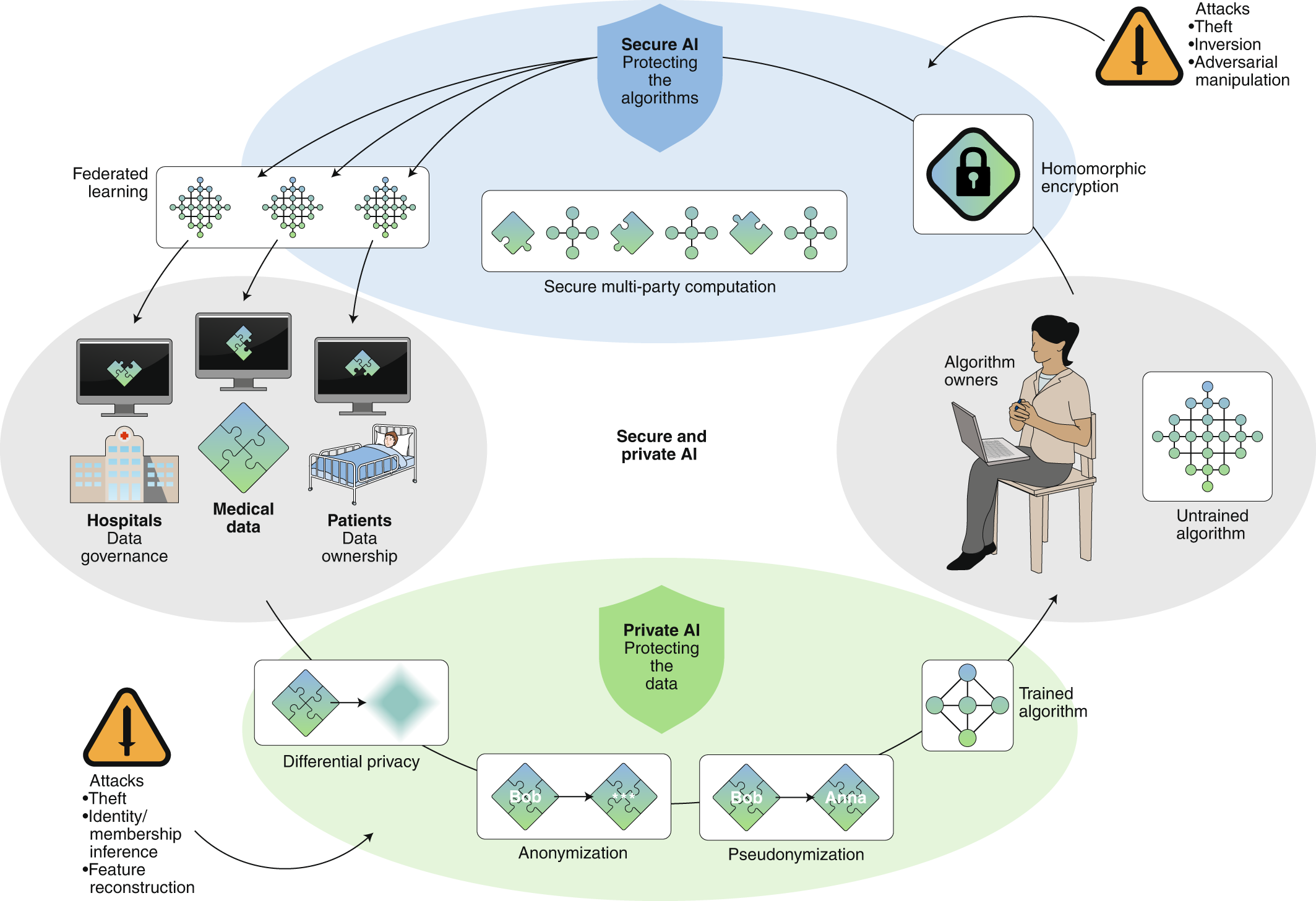
Secure, privacy-preserving and federated machine learning in medical imaging | Nature Machine Intelligence
Week 5 Reading Assignment: “Secure Multiparty Computation for Privacy-Preserving Data Mining“ Discussion Summary Question
![PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/54858338e517a3112133e7e664d762299842671b/5-Figure2-1.png)
PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar
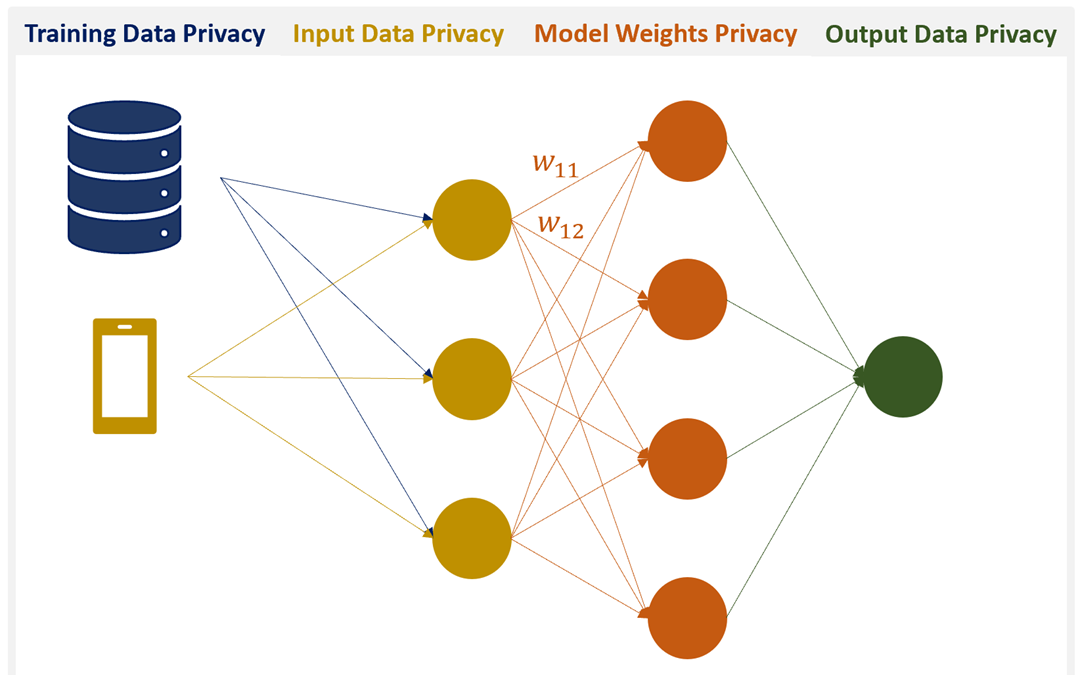
Perfectly Privacy-Preserving AI. What is it and how do we achieve it? | by Patricia Thaine | Towards Data Science
![PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/54858338e517a3112133e7e664d762299842671b/8-Figure4-1.png)
PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar

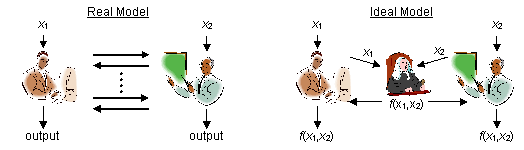








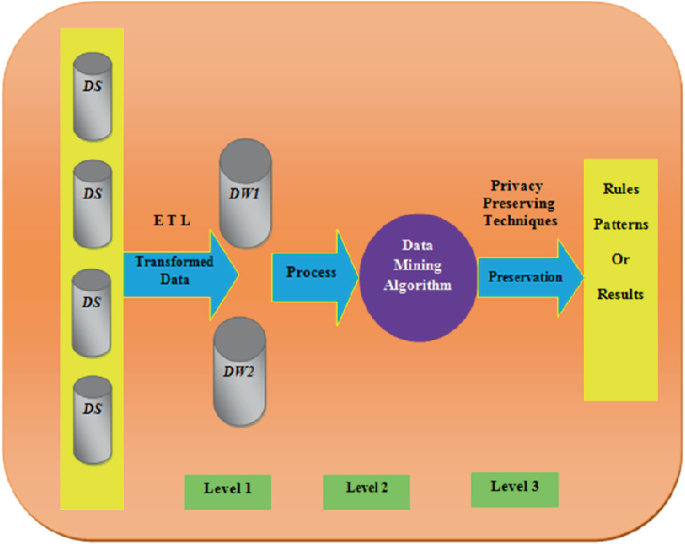
![PDF] Secure Multiparty Computation for Privacy-Preserving Data Mining | Semantic Scholar PDF] Secure Multiparty Computation for Privacy-Preserving Data Mining | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/55682d5db7f02b99ee979c3cda256b5db494c6fb/2-Figure1-1.png)